 【縛雞之見】
【縛雞之見】
所以,黑警解放軍攻進香港網路中心,豈是單純的治安目的。
想一想,香港網路資訊被控制的後果。
中國劫持西方國家關鍵的網路骨幹China has been 'hijacking the vital internet backbone of western countries' Catalin Cimpanu@ZDNet 20181026 Tzimocracy翻譯
Chinese government turned to local ISP for intelligence gathering after it
signed the Obama-Xi cyber pact in late 2015, researchers say.
研究人員說,中國政府在2015年底簽署了《歐巴馬-習近平》網路公約後,便轉向地方ISP收集情報。
A Chinese state-owned telecommunications company has been "hijacking
the vital internet backbone of western countries," according to an academic
paper published this week by researchers from the US Naval War College and Tel Aviv
University.
美國海軍戰爭學院和特拉維夫大學研究人員本週發表的一篇學術論文說,一家中國國有電信公司一直在「劫持西方國家關鍵的網路骨幹」。
SECURITY
- BlueKeep
exploit to get a fix for its BSOD problem
- Major
ASP.NET hosting provider infected by ransomware
- Apple
Mail on macOS leaves parts of encrypted emails in plaintext
- Fixing
data leaks in Jira (ZDNet YouTube)
- Best home security of 2019: Professional monitoring and
DIY (CNET)
- How to control location tracking on your iPhone in iOS 13
(TechRepublic)
The culprit is China Telecom, the country's third-largest telco and internet
service provider (ISP), which has had a presence inside North American networks
since the early 2000s when it created its first point-of-presence (PoP).
罪魁禍首是「中國電信」,該國第三大電信和網路服務提供商(ISP),自2000年代初創建其第一個數據中心的接入點(PoP)以來,它就已經在北美網路中佔有一席之地。
PoPs are data centers that do nothing more than re-route traffic between all
the smaller networks that make up the larger internet.
PoP是數據中心,它只不過在組成大型Internet的所有較小網路之間重新路由流量。
These smaller networks are known as "autonomous systems" (AS) and
they can be the networks of big tech companies like Google, your friendly neighborhood
ISP, big tier-1 ISPs like Verizon, university networks, bank networks, web hosting
companies, and all entities big enough to have received their own block of IP addresses.
這些較小的網路稱為「自治系統」(AS),它們可以是大型技術公司(如Google),您的友好鄰居ISP,大型1級ISP(如Verizon),大學網路,銀行網路,網路託管公司和 所有足夠大的實體都可以接收到自己的IP地址。
Traffic travels between these AS networks with the help of the Border Gateway
Protocol (BGP). This protocol was created in the early 80s and does not feature
any security controls, allowing anyone to announce a bad BGP route and receive traffic
that was not intended for their network.
借助邊界網關協議(BGP),流量在這些AS網路之間傳播。該協議創建於80年代初,不具有任何安全控制功能,因此任何人都可以宣布一條錯誤的BGP路由,並接收不是給他自己的網路流量。
In the vast majority of cases, these incidents --called BGP hijacks-- happen
because of configuration mistakes and are resolved in minutes or hours.
在大多數情況下,這些事件(稱為BGP劫持)是由於配置錯誤而發生的,可以在數分鐘或數小時內解決。
But there are also some networks that hijack BGP routes to send legitimate
traffic through malicious servers. They do this to carry out man-in-the-middle traffic
interception, phishing attacks to steal passwords, or to record HTTPS-encrypted
traffic to later decrypt it by leveraging cryptographic attacks such as DROWN or Logjam.
但是,也有一些網路劫持BGP路由,以惡意伺服器發送合法流量。他們這樣做是為了進行中間流量攔截,網路釣魚攻擊以竊取密碼,或者記錄HTTPS加密的流量,然後利用諸如DROWN或Logjam之類的加密攻擊對其進行解密。
In a research paper published this week, researchers reveal that China Telecom
has been one of the internet's most determined BGP hijackers around.
在本週發表的研究論文中,研究人員透露,中國電信一直是網路上最頑固的BGP劫持者之一。
Researchers point out that the Chinese government, through China Telecom,
has started abusing BGP hijacks after it entered into a pact with the US in September 2015 to stop all government-back cyber operations
aimed at intellectual property theft.
研究人員指出,中國政府已於2015年9月與美國達成一項協議,停止所有政府支持的旨在盜竊知識產權的網路運營活動,之後透過中國電信開始濫用BGP劫持行為。
"This necessitated new ways to get information while still technically
adhering to the agreement," said the researchers. "Since the agreement
only covered military activities, Chinese corporate state champions could be tasked
with taking up the slack. [...] Enter China Telecom."
研究人員說:「這需要新的方式來獲取信息,同時在技術上仍要遵守該協議。」「由於該協議僅涵蓋軍事活動,因此可能會要求中國的企業國家領導人承擔責任。進入中國電信。」
The research duo says they've built "a route tracing system monitoring
the BGP announcements and distinguishing patterns suggesting accidental or deliberate
hijacking."
這對研究人員說,他們已經建立了「一個路由跟踪系統,監視BGP公告並區分暗示意外或故意劫持的模式」。
Using this system, they tracked down long-lived BGP hijacks to the ten PoPs
--eight in the US and two in Canada-- that China Telecom has been silently and slowly
setting up in North America since the early 2000s.
他們使用此系統追踪了長期存在的BGP劫持,發現了10個PoP(美國為8個,加拿大為2個),自2000年代初以來,中國電信一直在北美默默地緩慢地建立它。
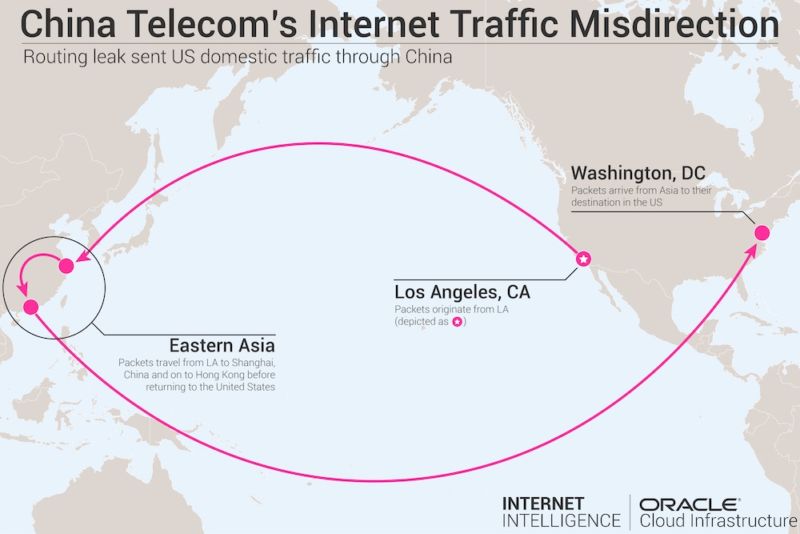
"Using these numerous PoPs, [China Telecom] has already relatively seamlessly
hijacked the domestic US and cross-US traffic and redirected it to China over days,
weeks, and months," researchers said.
研究人員說:「使用這些眾多的PoP,[中國電信]已經相對無縫地劫持了美國國內和跨美國的流量,並將其在幾天,幾周和幾個月內重定向到中國。」
"While one may argue such attacks can always be explained by normal'
BGP behavior, these, in particular, suggest malicious intent, precisely because
of their unusual transit characteristics -namely the lengthened routes and the abnormal
durations."
「儘管有人可能總是以正常的BGP行為來解釋這種攻擊,但這些攻擊尤其表明了惡意的意圖,正是由於它們具有異常的傳輸特性-即延長的路由和異常的持續時間。」
In their paper, the duo lists several long-lived BGP hijacks that have hijacked
traffic for a particular network, and have made it take a long detour through China
Telecom's network in mainland China, before letting it reach its intended and final
destination.
在他們的論文中,二人組列出了幾個長期存在的BGP劫持,這些劫持已經劫持了特定網路的流量,並使其繞開了中國電信中國大陸的網路,繞了很長時間,然後才到達預期的最終目的地。
- Starting from February 2016 and for about six months,
routes from Canada to Korean government sites were hijacked by China Telecom
and routed through China.
- 從2016年2月開始,大約六個月,中國電信劫持了從加拿大到韓國政府站點的路線,並通過中國。
- On October 2016, traffic from several locations
in the USA to a large Anglo-American bank headquarters in Milan, Italy was
hijacked by China Telecom to China.•
- 2016年10月,中國電信劫持了從美國多個地點到意大利米蘭的一家大型英美銀行總部的流量。
- Traffic from Sweden and Norway to the Japanese network
of a large American news organization was hijacked to China for about six weeks
in April/May 2017.
- 2017年4月/ 5月,從瑞典和挪威到美國大型新聞機構的日本網路的流量被劫持到中國約六週。
- Traffic to the mail server (and other IP addresses)
of a large financial company in Thailand was hijacked several times during
April, May, and July 2017. Some of the hijack attacks started in the USA.
- 在2017年4月,5月和7月,幾次劫持了泰國一家大型金融公司的郵件服務器(和其他IP地址)的流量。某些劫持攻擊始於美國。
Researchers also note that China's internet network is a system that's largely
closed off and isolated from the rest of the internet, to which it connects only
via three nodes located in Beijing, Shanghai, and Hong Kong.
研究人員還指出,中國的網路基本上是封閉的,與網路的其餘部分隔離,僅通過位於北京,上海和香港的三個節點連接到該網路。
This isolationist approach to its internet infrastructure means that China
wouldn't be able to carry out BGP hijacks for international traffic because very
little goes through its mainland nodes. This
is why the PoPs it set up in North America, but also throughout Europe and Asia,
are so crucial.
這種隔離主義的網路基礎設施方法,意味著中國將無法對國際流量進行BGP劫持,因為很少有穿越其內地節點的行為。這就是為什麼它需要在北美以及整個歐洲和亞洲建立如此重要的PoP的原因。
"That imbalance in access allows for malicious behavior by China through
China Telecom at a time and place of its choosing, while denying the same to the
US and its allies," researchers noted.
研究人員指出:「觸及量的不平衡,使得中國可以在選擇的時間和地點,透過中國電信進行惡意行為,而不考慮對美國及其盟國。」
"The prevalence of and demonstrated the ease with which one can simply
redirect and copy data by controlling key transit nodes buried in a nation's infrastructure
requires an urgent policy response."
「透過對國家基礎設施中關鍵傳輸節點的控制,可簡單地重新定向和複製數據的普遍性,這需要採取緊急政策措施。」
ZDNet readers can find out more from the research paper, entitled "China's
Maxim - Leave No Access Point Unexploited: The Hidden Story of China Telecom's BGP
Hijacking," which is available for download, here.
中國在模擬萬一在香港發動六四鎮壓,能在網路上如何破壞新聞傳播,達到最大阻絕效果。
回覆刪除